 |
Understaffed IT |
|
Augment IT | Find Gaps | Monitor & configure |
|
 |
Concerned management |
|
Compliance
| IT Audit
| Comprehensive IT
| Startup
Ransomware | Cybersecurity Insurance Questionnaires |
|
 |
DevOps, SRE, or MSP |
|
Code Security Review | Independent IT Audit | L3 |
|
Cybersecurity first • Customized for you
Balanced & Holistic Approach to Proactive IT
We get it: even the best system administrators can't fix all of your computer issues, deal with the cloud, stay on top of PCI and privacy compliance, stay abreast of emerging cybersecurity threats, and plan to reduce all of the problems they're solving.
Even with a team of developers, IT support staff, and outsourced “IT service” providers, you need proactive and holistic information technology and information security assessment, management, and tier-three support so you can stop having to react to IT problems, outages, and attacks.
We can even provide local remote and on-site Toronto, Vancouver, and Calgary IT Support.
Read More
Focused PCI, NERC, insurance, health, and privacy audits to in-depth customized comprehensive control assessments using our proven processes, proprietary tools, government and Fortune 50 audit experience, and advanced cybersecurity control certifications.
Whether your current “IT Department” is the founder who hands out laptops, a reactive outsourced IT company, or group of desktop support experts, ThreeShield will fill in the gaps to proactively increase reliability and support your current IT and non-IT staff with experienced IT and Information Security experts.
Anyone can install a server or wireless network; turn on a laptop; fill in a website template; or sign up for an AWS, Google Workspace, or Microsoft 365 account. However, it takes experts to securely configure, maintain, and monitor these systems to prevent outages and threats like ransomware.
Experience with accounting, aerospace, fintech, government, healthcare, law, oil & gas, retail, startups, and other sectors
Some of ThreeShield's Clients
ThreeShield Information Security has provided customized IT security tools and consulting to organizations of all sizes, including the following:
IT Architect, Financial Technology and Online Retail
Collaborating with ThreeShield to ensure data security was an exciting and educational experience. As we exploded in growth, it was clear that we needed to rapidly mature on all fronts, and ThreeShield was integral to building our confidence with information, software, and infrastructure security.

CTO, Tilia Inc. (Financial Technology and Online Payments)
As the Chief Compliance Officer of a payments entity, I have relied on ThreeShield Information Security to provide risk-based solutions that have satisfied regulators and business partners alike. While our Money Services Business is unique in that it supports commerce within virtual worlds and video game environments, the security standards that we have to meet are the same as they would be for any regulated financial institution.
ThreeShield has employed a dynamic, risk-based approach to information security that is specific to our business needs but also provides comfort to our external stakeholders.
I recommend their services.

IT Security Director, Linden Lab (Virtual Reality)
ThreeShield helped us focus our efforts, enhancing our security posture and verifying PCI compliance.
All of this was achieved with minimal disruption to the engineering organization as a whole.
The approach was smart. In a short time, we accomplished what much larger companies still struggle to achieve.

VP Operations and Platform Engineering
Chris [of ThreeShield] possesses the rare skill in security professionals of understanding broader business and technical demands and using that knowledge to develop a balanced approach to security. He skillfully avoids the dogmatic, prescriptive approach to security I've seen all too often and instead builds a security plan that genuinely strengthens the business.

Director of Customer Support
Chris [of ThreeShield] was keen on building partnerships of understanding with key stakeholders, and made the effort to understand the needs of the customer support team in terms of information, and balance those with the regulatory concerns -- both in specific and in general -- over PII, data storage and transmission, etc. It is this proactive approach that ensured that we had an open line of communication with Chris, and made me feel confident that when reaching out to him with a question or concern would net me a direct and actionable response.

Senior Director of Systems and Build Engineering
ThreeShield very much values active and respectful collaboration, and went out of their way to get feedback on policies to make sure proposals balanced business needs while not making employees feel like they were dealing with unreasonable overhead. By doing so ThreeShield really helped change the culture around security mindfulness is positive ways.
Blog
Information Technology and Information Security News
News & Blog
ThreeShield's clients receive security updates and proactive action to prevent the items in our block from affecting them before these issues hit the news.
Our blog includes a subset of this information delayed after clients are already protected.
View full blog

Cybersecurity News
EasyXDM Library 2.5.20 Vulnerabilities27 March 2023
Cross-site scripting, redirection and other vulnerabilities that we discovered
Cybersecurity News
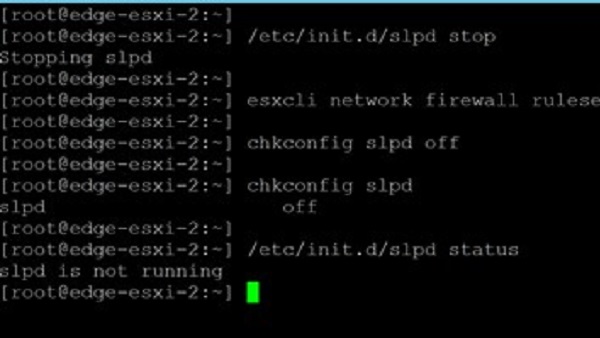
ESXiArgs VMWare Ransomware13 February 2023
Why ThreeShield's clients didn't get ESXiArgs ransomware and how you can prevent it or recover from it.
Phishing Trends
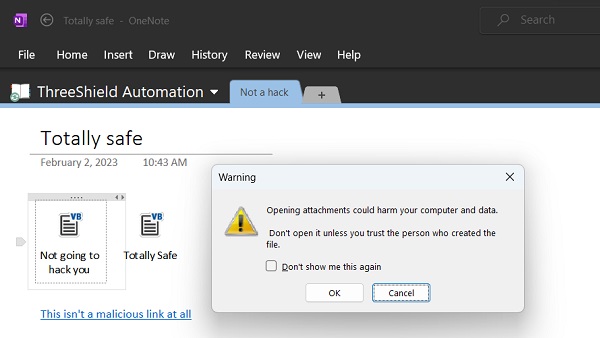
OneNote Phishing2 February 2023
What do do about the increase in OneNote phishing. Includes attachment extensions to quarantine.