OneNote: A good place to hide bad things
A few years ago, we started seeing the bad guys sending .html, .pdf, and .doc files as fake websites that tricked recipients into handing over their Microsoft, Google, Adobe, and banking passwords. However, after companies with proactive IT services like ThreeShield started to quarantine these sorts of attachments, the bad guys have moved to sharing malicious files through built-in Microsoft 365 file sharing and encrypted email services.
However, until recently, we didn't see much abuse of OneNote files. Something changed in the bad guy zeitgeist last month and we saw many more OneNote attachments coming in for us to review. We found:
- fake buttons that covered malicious .vbs scripts
- "security warnings" that opened malicious scripts and phishing pages
- "blurred out" backgrounds with a button to show the file (with malicious scripts behind the button)
- traditional links to tried-and-trusted Microsoft phishing login pages
What to do if you aren't quarantining OneNote files
By default, OneDrive displays a warning when you click on an script embedded in a OneNote file. However, if you clicked Don't show me this again, you might miss this warning. The best way to avoid these sorts of things is to slow down and force yourself to avoid hitting that OK button reflexively.
If you're a system administrator or MSP, set the following registry keys to 0 or delete them if they are present:
HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\OneNote\Options\EmbeddedFileOpenOptions\EmbeddedFileOpenWarningDisabled
HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\OneNote\Options\EmbeddedFileOpenOptions
If specfic file types are allowed, for example .html, you may see additional keys under
for example, .html with a DWORD value of 1. Set these to 0 or delete EmbeddedFileOpenOptions entirely.
What to quarantine?
In general, the strategy for quarantining attachments is to select file types that bad guys use more often than regular business contacts. For example, most businesses have modern versions of office, so they send .docx files; however, bad guys exploit some of the old macro capabilities in older versions of Word, so they use .doc files.
Some businesses use compressed file formats like .zip on a regular basis; however, more bad guys use them to send files without getting the "mark of the web" that Microsoft uses to display more warnings for files downloaded from the Internet.
Most legitimate disk images (like .iso files) are too large to be sent by email; however, bad guys use this format in the same way as .zip files
Before implementing this list, you'll want to go through email traces to see companies that routinely receive these sorts of files. For exmaple, some banks still send .html and outdated versions of .doc files. We have these as exceptions to the rules for all of our new clients and some tweaks for some of the following extensions:
- .7z
- .ace
- .com
- .doc
- .exe
- .gz
- .js
- .hta
- .htm
- .html
- .img
- .iso
- .mht
- .one
- .onepkg
- .onetoc
- .onetoc2
- .ppt
- .rtf
- .tar
- .vbs
- .xll
- .ls
- .zip
What our clients say about ThreeShield

CTO, Tilia Inc. (Financial Technology and Online Payments)
" ThreeShield has employed a dynamic, risk-based approach to information security that is specific to our business needs but also provides comfort to our external stakeholders. I recommend their services. "

IT Architect, Financial Technology and Online Retail
" Collaborating with ThreeShield to ensure data security was an exciting and educational experience. As we exploded in growth, it was clear that we needed to rapidly mature on all fronts, and ThreeShield was integral to building our confidence with information, software, and infrastructure security. "

IT Security Director, Linden Lab (Virtual Reality)
" ThreeShield helped us focus our efforts, enhancing our security posture and verifying PCI compliance.
All of this was achieved with minimal disruption to the engineering organization as a whole.
The approach was smart. In a short time, we accomplished what much larger companies still struggle to achieve. "

Senior Director of Systems and Build Engineering
" ThreeShield very much values active and respectful collaboration, and went out of their way to get feedback on policies to make sure proposals balanced business needs while not making employees feel like they were dealing with unreasonable overhead. By doing so ThreeShield really helped change the culture around security mindfulness is positive ways. "
Popular Technical Articles

29 January 2024
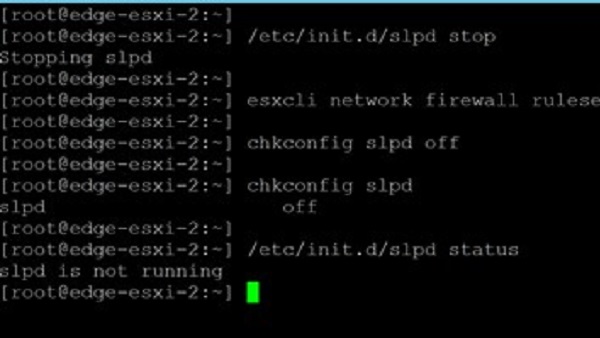
13 February 2023
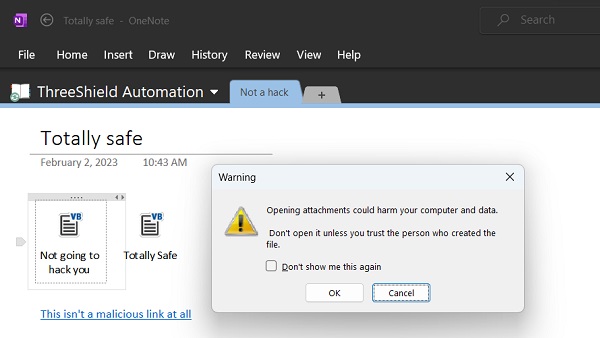
2 February 2023
16 January 2023

26 March 2021
